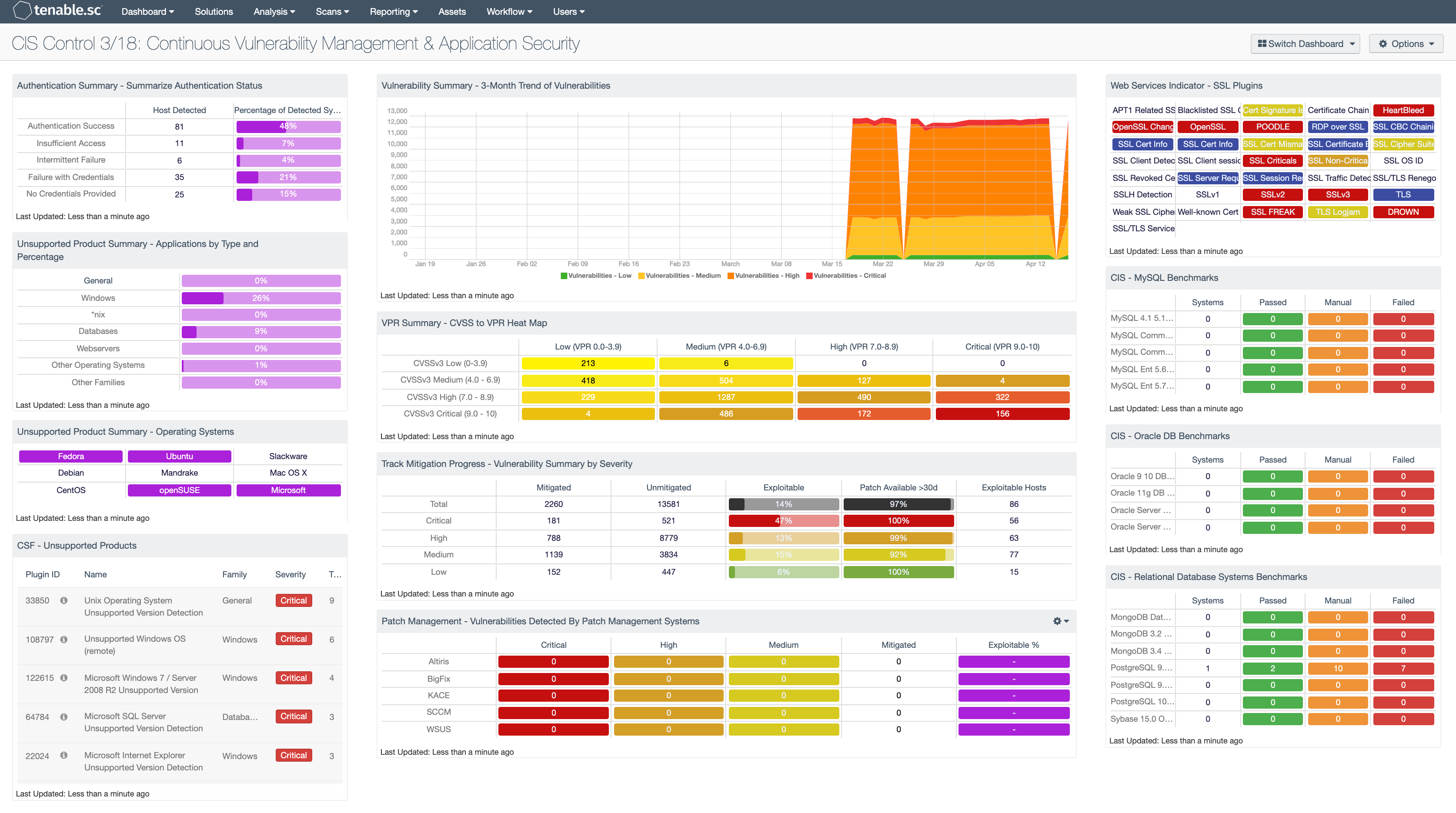
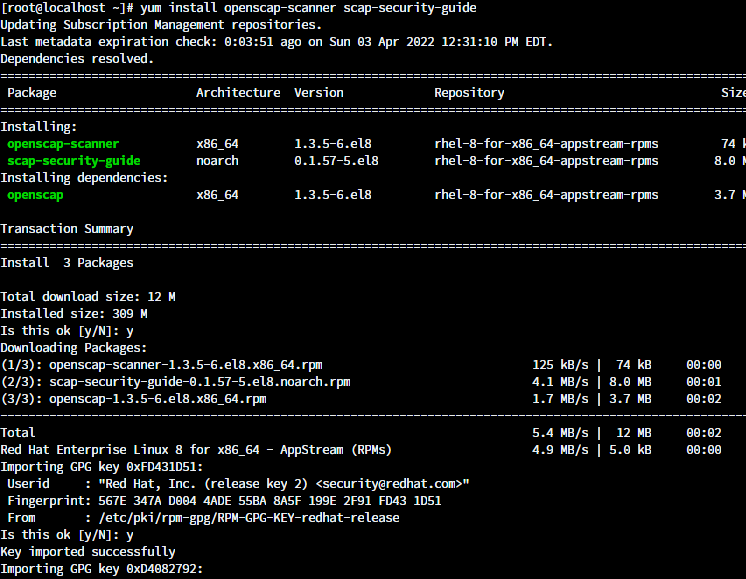
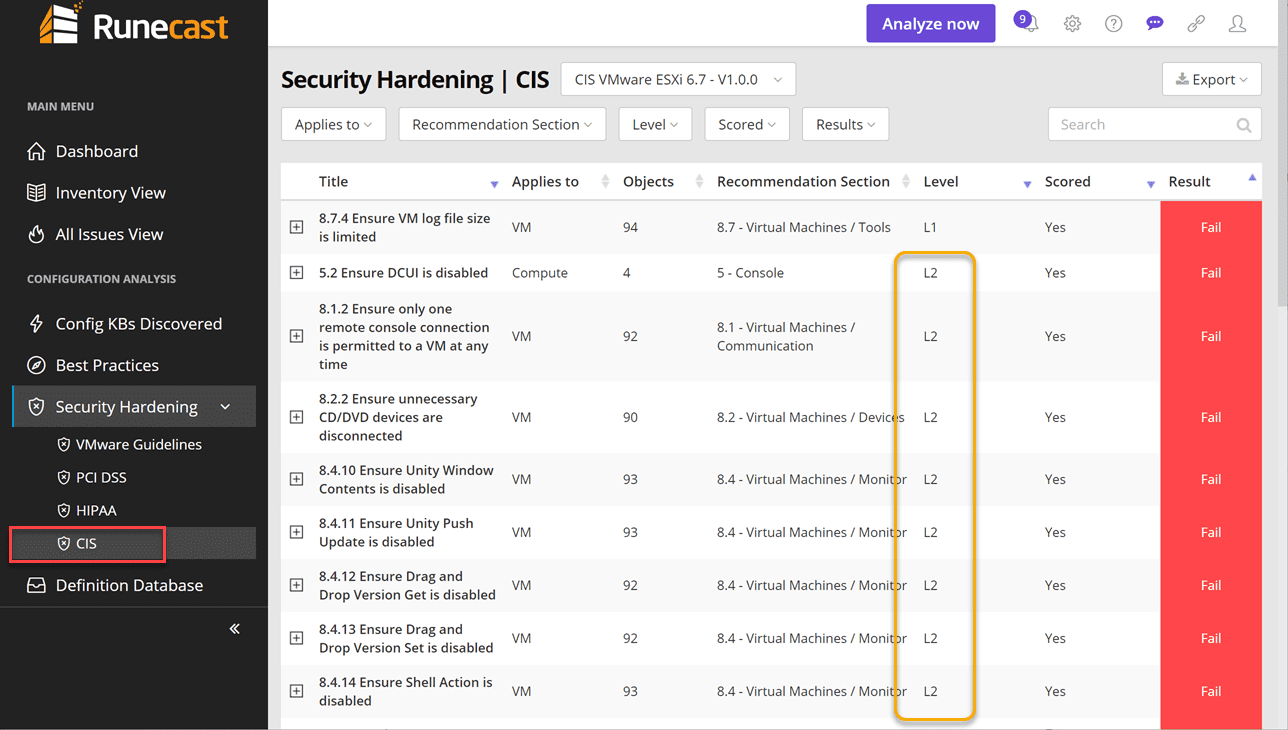
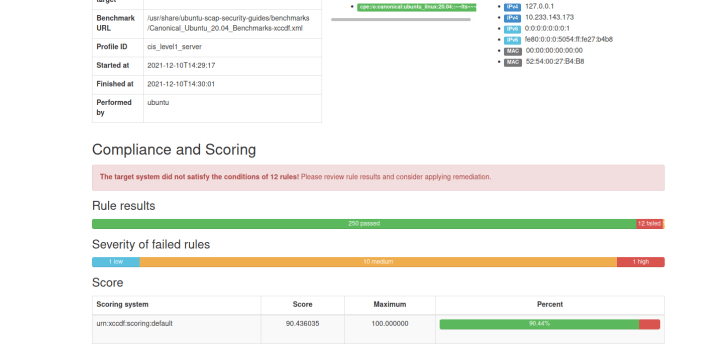
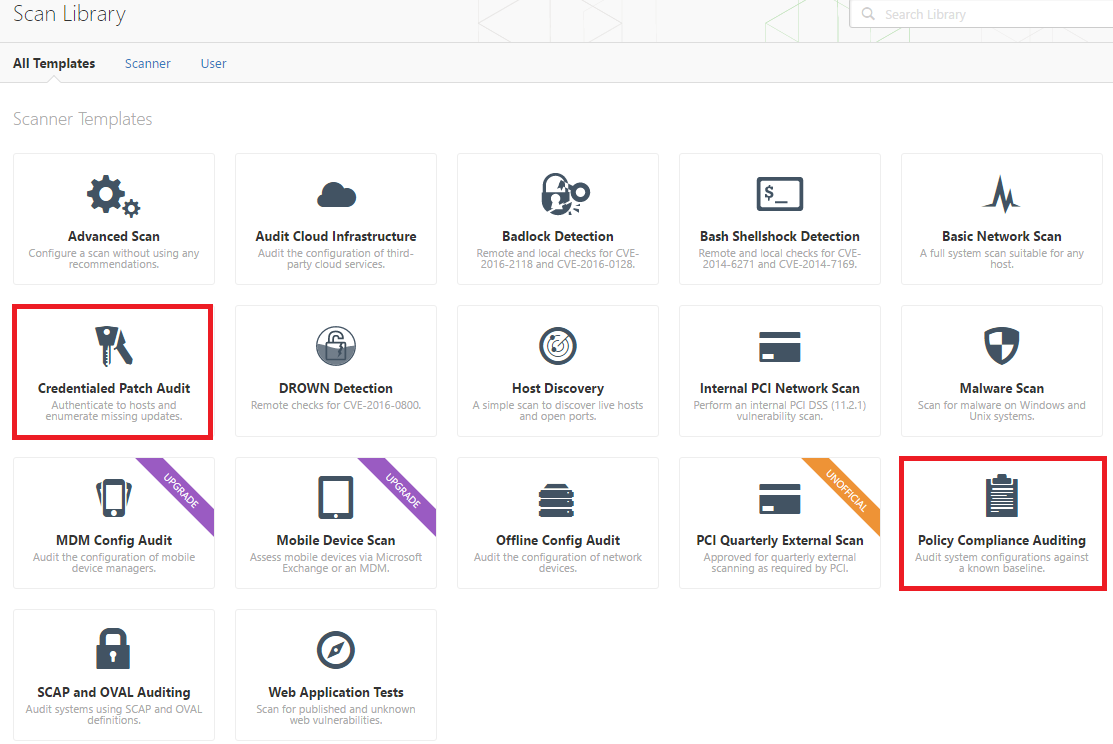
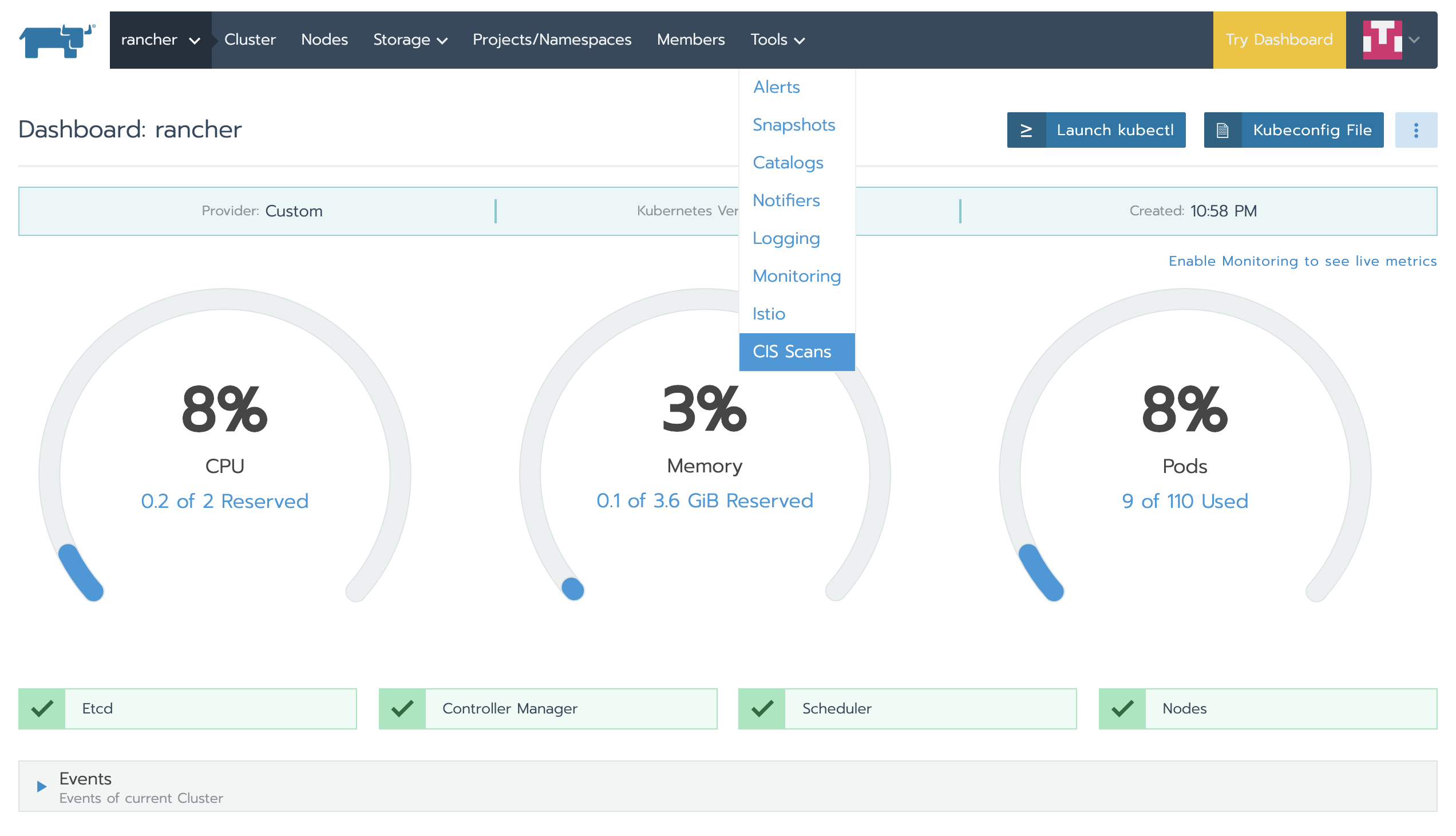
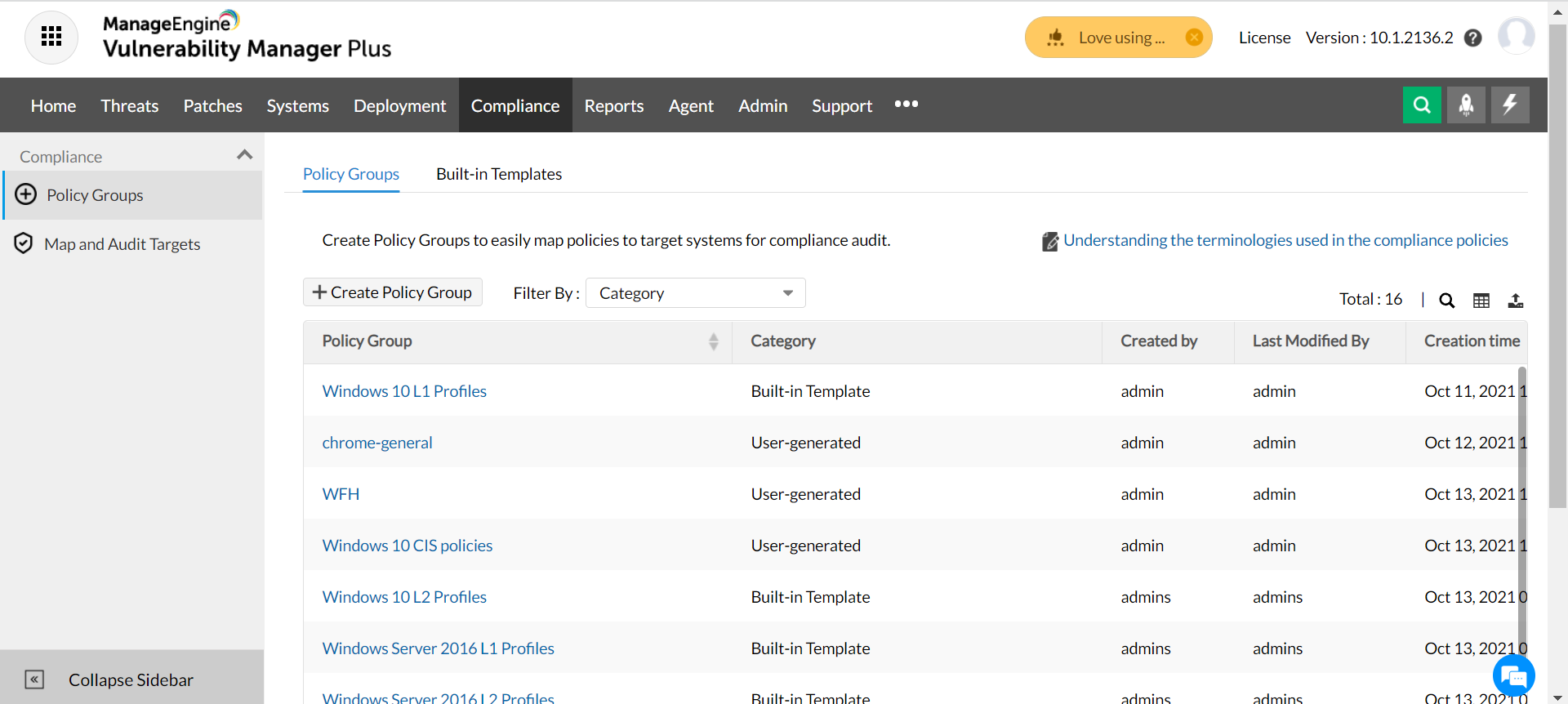
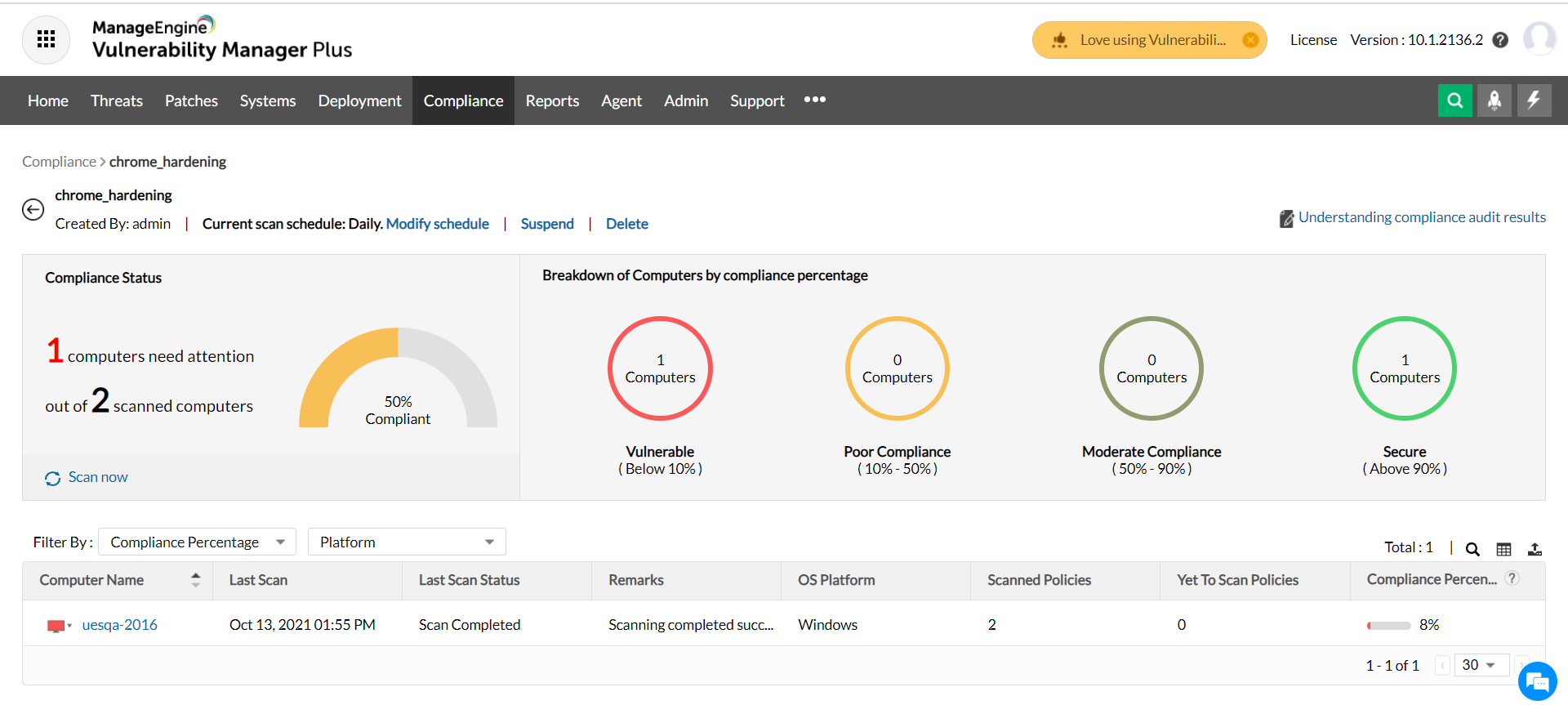
PDF) Automation of information security audit in the Information System on the example of a standard "CIS Palo Alto 8 Firewall Benchmark"

Artiën on Twitter: "Playing with #Kibana #Elasticsearch with my #nessus2es trying to see what kind of #compliance info I can get out of a #Nessus CIS Benchmark scan. Pretty happy with how